- 0 Posts
- 22 Comments

 0·3 days ago
0·3 days agoDude shot the messenger instead of facing the issue at hand.

 0·3 days ago
0·3 days agoTor Network.
I2P.
Autonomi.

 0·11 days ago
0·11 days agoNo, its still 45 days

 0·12 days ago
0·12 days agoTurning off secure boot wont turn off your TPM, it just turns off all the signature verifications. Your TPM still stores the decryption keys and you can still decrypt your data.
Now if you do a UEFI/BIOS update without disabling your encryption while using a TPM, and dont have password decryption as a backup, yes, you could potentially lose access to your data.

 0·13 days ago
0·13 days agoNo way. I would looooove a screenshot of this tweet
Edit:
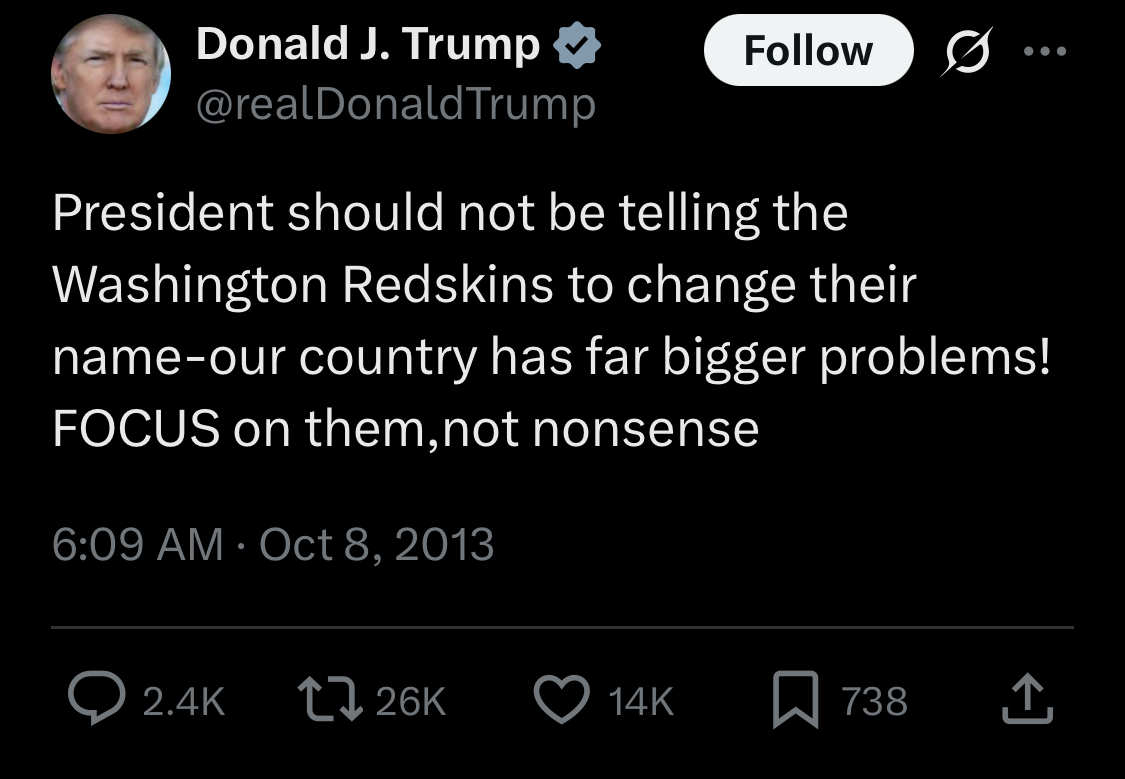

 0·14 days ago
0·14 days agoSounds like the devs have spoken then.

 0·14 days ago
0·14 days agoIts funny because the release notes for their December '21 BIOS update says:
Major vulnerabilities updates, customers are strongly encouraged to update to this release at the earliest.
And many of their release notes say that they fix security issues. I would say that supercedes the footnote at the bottom that says to update your BIOS only if you’re having issues.
Plus, doesn’t Gigabyte have A/B BIOS updates? So if you have a failed flash, you can switch to the previous BIOS that was working?

 0·14 days ago
0·14 days agoNo.
You want it, build it yourself.

 0·14 days ago
0·14 days agoSome vendors still have a red flag on their support page discouraging uefi updates unless you’re actively experiencing problems.
I dont know which vendor you are referring to, but that is a horrible practice. There should be active support and release notes stating that “This release is a security fix” at a bare minimum. If your motherboard manufacturer does not offer that, then I could never recommend them to someone. They need to be held to a higher standard.
At least from my experience, ASUS, Dell, and Apple will publish that information.

 0·14 days ago
0·14 days agoEven if the code is there, you will need someone to maintain that code. Easier or not, even in a git repository, those individual components will eventually not have the support necessary to patch it.
If an eight year old usb controller has flaws, and the manufacturer is not maintaining that git repository anymore because they cannot possibly afford to hire someone to look at that code after so long, then it is going to keep those flaws. It wont matter if that code is proprietary or open source and included in coreboot. Its just simply not feasible to support hardware properly once most of the world has moved on to other products.

 0·15 days ago
0·15 days agoGenerally, motherboard manufacturers source their components from other companies. They do not manufacture the entire board themselves. This includes CPUs, Wifi cards, USB controllers, bluetooth, audio, display controllers, etc. Each and every one of them create new products, maintain their own firmware for all those new products, and push updates to the motherboard manufacturers when there are updates.
Coreboot/libreboot do not update those components themselves. They also must be provided that source code.
Just for coreboot alone, the last release had more than 120 contributors push over 900 commits. One person is not able to maintain that piece of software, as it is an enormous task.

 0·15 days ago
0·15 days agoAMD are generally quick with providing microcode updates. Once they have them, they provide them to your motherboard manufacturer to include in a firmware update. This is the part that usually takes a while, if done at all.

 0·15 days ago
0·15 days agoNo idea. You can use something like jackett to generate an RSS feed for you if they dont have one.
Maybe they have a newsletter for updates, or a registration card, social media account, or maybe a security team that announces security updates.
All im suggesting is look into how your manufacturer announces these updates and actively listen to that communication.

 0·15 days ago
0·15 days agoIMO, keep an rss feed of your vendors firmware updates being released on their website or periodically check it yourself. As soon as its released, go ahead and install it. If you want to be cautious, maybe give it a week or two to make sure they dont pull the update due to issues with that particular release.
Even better, if the manufacturer offers a utility to keep updates installed, just run that periodically.

 0·15 days ago
0·15 days agoAs much as I would like to agree with that, each piece of hardware is going to have its own niche set of problems that the coreboot/libreboot team is not going to research and maintain. It wont be because they dont want to. They just dont have the resources and source code from the vendors. You will get your standardized updates, but it will not cover a lot of the proprietary blobs necessary for the hardware to operate.
Once the vendor stops supporting it, thats it. Its a ticking time bomb. Its how we get articles like the one in the OP. The vendor and user are not going to put in work to keep this updated. Even if they had coreboot/libreboot, it wont get updated.
Its a shitty thing that isn’t easy to solve except by tying in hardware and software into single, unified products that are written in perfect code. Its not possible.

 0·15 days ago
0·15 days agoI know Ill get flak for this, but you shouldn’t be using end-of-life hardware, including motherboards. Once the vendor stops providing firmware updates, its time to look at replacing that hardware. It doesn’t matter what operating system you use, if there are hardware vulnerabilities, then your OS isn’t able to properly protect you.
If your hardware is still supported, you should regularly be updating the firmware.

 0·16 days ago
0·16 days agoI believe thats how Android works. As I recall, it uses fscrypt.
It steals from the copyright holders in order to make corporate AI money without giving back to the creators.
It uses insane amounts of water and energy to function, with demand not being throttled by these companies.
It gives misleading, misquoted, misinformed, and sometimes just flat out wrong information, but abuses its very confidence-inspiring language skills to pass it off as the correct answer. You HAVE to double check all its work.
And if you think about it, it doesn’t actually want to lick a lollipop, even if it says it does. Its not sentient. I repeat, its not alive. The current design is a tool at best.